Article
Going on offense: Filling the gaps in healthcare cybersecurity
In my cybersecurity-1/”>first blog of this series, I discussed the basics of offensive cybersecurity and its role in a comprehensive security program. The second installment explored some of the challenges organizations might face when deciding whether or not to implement this strategy and why those barriers to implementation shouldn’t make you hesitate to continue pursuing offensive cybersecurity tactics. Today, in the final chapter of this series, I will delve into how offensive cybersecurity can fill in the gaps left by traditional cybersecurity programs, particularly as it pertains to healthcare.
The gaps
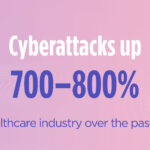
Despite the increase in cybersecurity spending in all sectors and industries, the prevalence of successful cyberattacks is still growing. In the healthcare industry, the prevalence of cyberattacks has risen steadily in the past six years (up 700–800%). Fortunately, the cybersecurity research and literary community has a pretty good consensus on some of the gaps that are contributing to poor cybersecurity results. These gaps include:
- organizations that are reactive when it comes to cybersecurity instead of proactive,
- responses to cybersecurity incidents that need to occur more quickly,
- awareness and understanding of cybersecurity best practices that need to be improved,
- and organizations that need to improve their understanding of their environments to include the strengths and weaknesses of the security program.
So how can offensive cybersecurity address these gaps and help slow the growth of attacks occurring?
Proactive over reactive
Traditional cybersecurity solutions are inherently reactive in nature. In order for your anti-virus to work, an attack, like a malicious file or piece of malware being downloaded, has to occur. This means that organizations do not begin to understand the issues that allowed the attack to occur until well after the damage has already been done. This concept would be similar to a cardiac patient who doesn’t try to implement a healthy lifestyle until after a major malfunction like a heart attack. Many times, it’s too little, too late.
However, offensive security testing can help organizations become (and stay) more proactive. If an organization performs offensive cybersecurity testing on themselves, they are looking for those issues that could lead to an attack before an actual attack occurs. This way, organizations can work to understand and fix security issues before they are exploited by attackers.
Real-time cybersecurity response
Historical data on cyberattacks highlights a serious issue: it takes the average organization too long to realize they’ve been attacked in order to effectively respond and prevent additional damage. The healthcare industry was the second worst in response times, averaging 255 days to detect a cyberattack. Like an infection to the body, cyberattacks need to be noticed and responded to as quickly as possible to prevent the spreading of negative impacts.
The old adage “practice makes perfect” definitely applies to this concept. Even in organizations with active security monitoring programs, the programs can always benefit from improvements and practice. Offensive cybersecurity programs can uniquely provide the opportunity for this to occur. As offensive cybersecurity personnel perform simulated attacks on an organization, the organization can measure its ability to detect the attacks and be more ready to respond to an actual attack.
Cyber awareness
Few people, if any, enjoy mandatory cybersecurity training, which could play a role in a lack of awareness of cybersecurity best practices. Traditional training programs revolve around explaining the “rules” of what needs to be done, but don’t help employees understand why.
Offensive cybersecurity professionals make great candidates to help explain this process as they operate with the same mindset of a real attacker during testing. Aside from the added intrigue of discussing cybersecurity concepts from the perspective of the criminal element, sharing this mindset with employees can help them better understand “the why” behind cybersecurity policies.
For instance, phishing attacks remain the most prevalent type of attack for healthcare organizations globally, and, at Altera Digital Health, anti-phishing training that focused on how hackers perform this type of attack was extremely well-received.
Like an infection to the body, cyberattacks need to be noticed and responded to as quickly as possible to prevent the spreading of negative impacts.
Understanding the cyber environment
While cybersecurity programs are generally conceptualized as a huge brick wall surrounding a castle, where the components are simple and easily compatible (bricks and mortar), I think it is more accurate to look at programs like a basket. Cybersecurity programs must integrate tools, talent and procedures like individual strands making up a basket. When examined closely, it is much harder to understand how well the fibers of a basket protect contents than a castle wall, highlighting the challenges organizations have in understanding their environments.
Rather than painstakingly going through the walls of the basket, fiber by fiber, to assess its efficacy, it would be more effective if we filled the basket with water and notated the leaks. In this metaphor, offensive cybersecurity personnel act like water—a flexible and determined force looking to flow freely. Through these actions, organizations can more easily understand where their “basket” has gaps that need to be fixed.
Continuing on
By now, I hope to have made clear that offensive cybersecurity has the potential to help solve the universal issues plaguing cybersecurity programs in a manner that justifies overcoming the challenges of implementation. With the importance of cybersecurity to the success of modern businesses, perhaps we will see more offensive cybersecurity programs within organizations in the future.