Article
Hackers are taking your password seriously. You should too.
I’m sure you’ve heard the phrase “Hackers aren’t breaking into systems. They’re logging in,” or some other variation. And it’s true—81% of data breaches start with compromised credentials. But I’m not going to give you another lecture about the importance of having separate passwords for each system or a listicle on ways to create stronger passwords. Because, let’s be honest, we’ve heard it a million times and keeping up with multiple, complex passwords is, quite frankly, annoying. It’s easy to ignore my advice, slip into complacency and reuse the same password over and over because it makes life easier.
Instead, I’m going to give you a peek behind the curtain, into the mindset of a hacker. This is a much more effective way to understand the very real threat a weak password poses to you and your organization. You’ll learn more about the strategies hackers use to compromise systems, see just how easy it can be to crack a password and gain a deeper understanding of the financial motivations behind these attacks. Let’s dive in.
The anatomy of a password
Your password consists of two key ingredients: length and complexity. Length is the total number of characters in your password. Complexity is the number and type of available characters to use in a password (e.g., special characters, symbols, capital letters, etc.).
We can put this into a simple equation to determine how long it may take a hacker to crack a password.
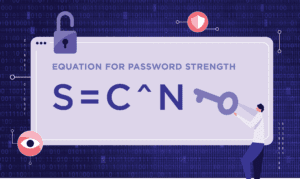
Based on this formula, the length of your password is the single biggest factor in determining how difficult it is to crack your password. Let’s look at a couple of examples.

Using the formula from earlier, we can determine that there are 1,934,917,632 possible password combinations in the first example. Sounds like a lot, right? Guess again. Using the right tools, a hacker can crack this password in just 77 seconds.
In the second example, the formula tells us that there are 141,167,100,000,000 possible password combinations. Using the same tools from earlier, it would take a hacker 10.47 years to crack this password.
As you can see, a lengthy password can go a long way in protecting your data. However, don’t discount the importance of complexity, as it makes it harder for your password to be guessed or “brute forced.” We’ll take a look at how that’s accomplished next.
Tools of the trade
There are several tools and strategies hackers can employ to get faster results. How quickly these tools work is determined by both the length and complexity of your password. These include:
Computers optimized for password cracking: These systems are capable of up to 350 billion password guesses per second.
Patterns: Guessing your password using common words, common usage of numbers/symbols etc.
Tuning: Hackers can improve their password guesses by doing research into your digital footprint on platforms like social media. They look for pet names, birthdays, family members, hobbies, etc., that might be used in your password.
Rainbow Tables: Precompiled lists of hacked passwords. This technique greatly increases the speed at which a hacking tool can guess passwords.
Dictionaries: Precompiled lists of words applicable to the target. Password dictionaries can include specifics from pattern generation and tuning activities performed by the hacker.
Password Profits
Let’s say you used a simple password, something that was cracked in just a few minutes. The hacker has your credentials. What could they do with them?
Direct attacks: Directly using compromised passwords to perform attacks and steal data.
Access Sales: Selling batches of compromised usernames/passwords to other hackers for their malicious purposes. Depending on what a password is used for, it could be sold on the dark web for thousands of dollars for a single one. Even social media account passwords (generally the cheapest) can fetch $10–15 apiece.
Enslaving: Using compromised credentials to take control of systems to add to botnets. Hackers have been found to advertise botnet services on the dark web for up to $7,500 per day.
Fraud: Stealing your digital identity to open bank accounts, purchase goods, etc.
In 2023, the average cost of a data breach for a healthcare business is $10M. And like I said earlier, 81% of data breaches begin with compromised credentials. Hackers have a lot to gain by accessing your systems, while you have everything to lose. So, the next time you have to update or create a new password, resist the urge to reuse an old password or use something easy like “Password1234.” Your data depends on it.
Want tips on how to create stronger passwords? Check out this blog by my colleague and the head of Altera’s CyberDefense Team, Jennifer Henninger.